As technology continues to reshape industries, cybersecurity sits firmly at the top of every executive’s agenda. The year 2025 is shaping up to be a turning point, with new attack surfaces, regulatory demands, and advanced defense strategies reshaping how organizations protect their digital assets.
For CTOs, the challenge is twofold: staying ahead of increasingly sophisticated threats while enabling innovation and growth. Falling behind on cybersecurity is no longer an option—it directly impacts brand reputation, customer trust, and business continuity.
This article explores the key cybersecurity trends every CTO must watch in 2025, along with practical insights to help you prepare your organization for what lies ahead.
Why Cybersecurity Demands CTO Attention in 2025
CTOs have always played a central role in digital transformation. But in today’s environment, their decisions on security frameworks, vendor choices, and compliance strategies can make or break an organization.
Here’s why 2025 is a pivotal year for CTOs:
- Attackers are evolving faster than ever. AI-driven attacks, ransomware-as-a-service, and deepfake social engineering tactics are on the rise.
- Regulators are cracking down. Global laws around privacy, data sovereignty, and AI governance are becoming stricter.
- Business operations are more connected. Hybrid work, IoT devices, and cloud-native infrastructures expand the attack surface.
- Customers expect more. Trust and transparency are now competitive differentiators.
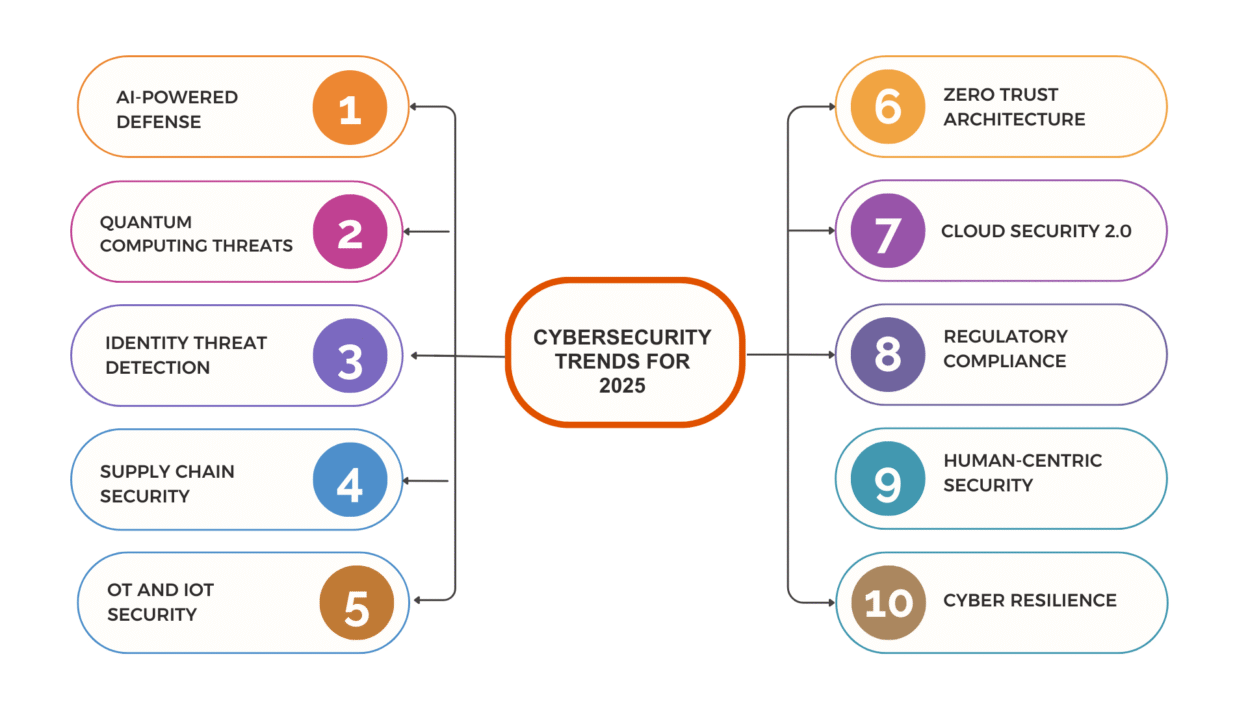
Top Cybersecurity Trends for CTOs in 2025
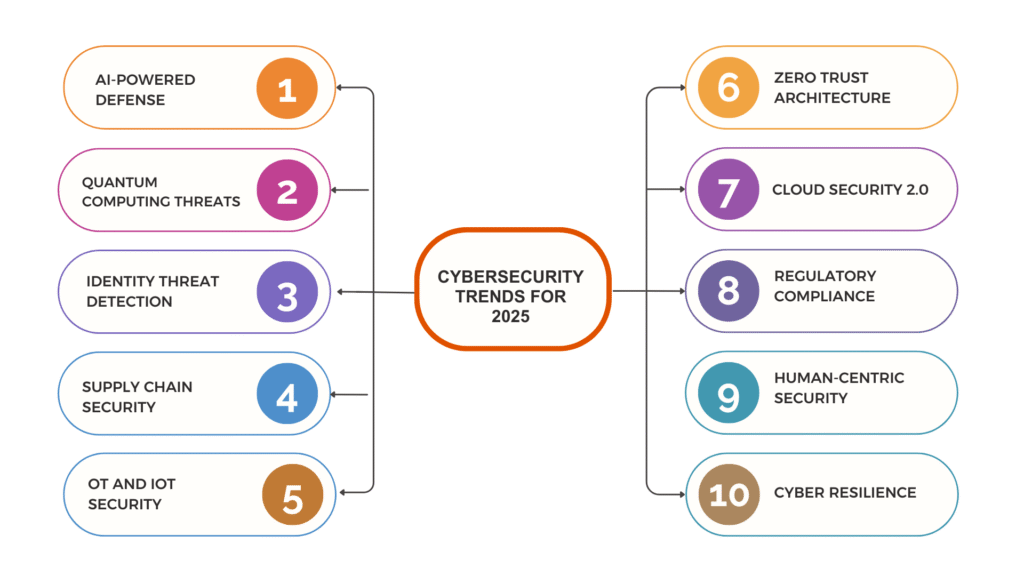
1. AI-Powered Cyberattacks and AI-Driven Defense
Artificial intelligence has become a double-edged sword. On one side, attackers use AI to automate phishing campaigns, generate deepfake content, and discover vulnerabilities faster. On the other, security leaders are deploying AI to detect anomalies, stop intrusions in real time, and strengthen threat intelligence.
CTO Insight:
- Expect to integrate AI-based defense tools into your SOC (Security Operations Center).
- Prioritize transparency—ensure your AI-driven security systems are explainable to comply with regulatory expectations.
2. Zero Trust Becomes the Standard
The “never trust, always verify” approach of Zero Trust architecture is no longer optional—it’s the baseline. With hybrid work models, BYOD (Bring Your Own Device), and multi-cloud environments, perimeter-based defenses are outdated.
CTO Insight:
- Accelerate Zero Trust adoption across identity, endpoints, and applications.
- Implement continuous authentication and micro-segmentation to minimize lateral movement.
3. Quantum Computing Threats on the Horizon
While large-scale quantum computers are still emerging, 2025 is the year CTOs must start preparing. Quantum computing has the potential to break traditional encryption, making today’s secure systems vulnerable tomorrow.
CTO Insight:
- Begin testing post-quantum cryptography solutions recommended by organizations like NIST.
- Map critical assets that depend on long-term data confidentiality.
4. Cloud Security 2.0
Cloud adoption continues to surge, but so do cloud-native risks: misconfigurations, shadow IT, and supply chain vulnerabilities. In 2025, cloud security strategies will go beyond traditional workload protection.
CTO Insight:
- Adopt Cloud-Native Application Protection Platforms (CNAPPs) to unify security.
- Ensure DevSecOps practices are embedded into the software lifecycle.
- Demand visibility into third-party vendors and cloud providers.
5. Rise of Identity Threat Detection and Response (ITDR)
Stolen credentials remain the most common entry point for attackers. Identity Threat Detection and Response (ITDR) has emerged as a critical layer of defense, focusing on real-time detection of account takeovers and lateral identity abuse.
CTO Insight:
- Integrate ITDR solutions with IAM (Identity Access Management).
- Educate employees and partners on identity hygiene practices.
6. Regulatory Pressure and Compliance-First Security
From GDPR updates to new AI regulations in the EU and U.S., compliance is no longer just about avoiding fines—it’s about enabling trust. In 2025, CTOs must design systems with compliance baked in from the start.
CTO Insight:
- Anticipate stricter rules around data residency, AI transparency, and incident reporting.
- Partner with legal and compliance teams early in the technology planning cycle.
7. Supply Chain Security Takes Center Stage
Attacks like SolarWinds proved how vulnerable supply chains are. By 2025, securing the extended ecosystem of vendors, SaaS providers, and third-party developers will be a top priority.
CTO Insight:
- Require security attestations and certifications from vendors.
- Adopt SBOMs (Software Bill of Materials) for transparency in open-source dependencies.
8. Human-Centric Security and Culture Building
Technology alone can’t solve cybersecurity challenges—human error remains a leading cause of breaches. In 2025, forward-thinking CTOs are prioritizing security culture, gamified training, and employee accountability.
CTO Insight:
- Shift from annual training sessions to continuous awareness programs.
- Use AI-driven simulations to replicate phishing or insider threats.
9. Operational Technology (OT) and IoT Security
As industries like manufacturing, healthcare, and energy digitize, IoT and OT devices are exploding in number. Unfortunately, they often lack strong security protocols.
CTO Insight:
- Map and segment IoT/OT devices to prevent network-wide compromise.
- Push for secure-by-design standards with IoT vendors.
10. Cyber Resilience and Incident Response 2.0
Preventing every cyberattack is impossible. The new benchmark is resilience—how quickly an organization can detect, respond, and recover.
CTO Insight:
- Establish playbooks for ransomware, insider threats, and supply chain breaches.
- Regularly test incident response with red-team/blue-team exercises.
Challenges CTOs Will Face in Implementing These Trends
While the above trends show where the industry is heading, CTOs will encounter roadblocks:
- Budget Constraints: Balancing innovation with rising cybersecurity costs.
- Talent Shortages: The global cybersecurity skills gap is expected to persist.
- Integration Complexity: Orchestrating multiple tools into a unified security ecosystem.
- Boardroom Buy-In: Translating cybersecurity risks into business language for executives.
Strategic Actions for CTOs in 2025
To stay ahead of these challenges, CTOs should:
- Adopt a Risk-First Approach: Focus on protecting the most business-critical assets.
- Invest in Automation: Use AI and automation to counter the talent shortage.
- Foster Collaboration: Break silos between IT, security, legal, and operations teams.
- Plan for the Long Term: Begin preparing now for quantum-safe security and future regulations.
- Measure and Report: Track KPIs such as mean time to detect (MTTD) and mean time to respond (MTTR).
Looking Ahead: Cybersecurity as a Business Enabler
Cybersecurity is no longer a back-office function—it’s a core business enabler. CTOs who treat it as such will not only protect their organizations but also unlock competitive advantage. Whether it’s securing customer trust, enabling new digital services, or ensuring compliance, the CTO’s cybersecurity strategy in 2025 will define business success.
The companies that thrive will be those that move beyond reactive security to proactive resilience—anticipating threats, embedding security into innovation, and adapting to a rapidly shifting landscape.
Final Thoughts
As a CTO in 2025, your role in cybersecurity is both technical and strategic. The trends outlined—AI, Zero Trust, quantum readiness, ITDR, compliance, and beyond—are shaping the next era of defense. Staying ahead requires a mindset of continuous evolution, not just periodic upgrades.
Cybersecurity will remain a moving target, but with the right investments in people, processes, and technology, you can transform it from a challenge into a strategic advantage.
The future belongs to organizations that make security not just a checkbox, but a core part of their DNA.